CentOS 7 安装openvpn的步骤详解
检查系统环境
[root@ss-usa-odo01 ~]# cat /etc/redhat-release
CentOS Linux release 7.0.1406 (Core)
[root@ss-usa-odo01 ~]# df -hP
Filesystem Size Used Avail Use% Mounted on
/dev/ploop12288p1 30G 484M 28G 2% /
devtmpfs 256M 0 256M 0% /dev
tmpfs 256M 0 256M 0% /dev/shm
tmpfs 256M 88K 256M 1% /run
tmpfs 256M 0 256M 0% /sys/fs/cgroup
[root@ss-usa-odo01 ~]# cat /dev/net/tun
cat: /dev/net/tun: File descriptor in bad state
[root@ss-usa-odo01 ~]# grep IPADDR /etc/sysconfig/network-scripts/ifcfg-venet0:0 | awk -F= '{print $2}'
104.223.122.202
[root@ss-usa-odo01 ~]#
系统初始化下
[root@ss-usa-odo01 ~]# curl -Lks onekey.sh/centos_init|bash
[root@ss-usa-odo01 ~]# reboot
更新源
[root@ss-usa-odo01 ~]# yum clean all && yum makecache && yum install epel-release -y && yum update -y
将CentOS 7的FrieWall换成iptables
bash -c "$(curl -Ls onekey.sh/friewall2iptables)"
yum安装openvpn
[root@ss-usa-odo01 ~]# yum install openvpn easy-rsa net-tools -y
配置openvpn Server端
[root@ss-usa-odo01 ~]# cp /usr/share/doc/openvpn-2.3.11/sample/sample-config-files/server.conf /etc/openvpn/
[root@ss-usa-odo01 ~]# mkdir /etc/openvpn/easy-rsa
[root@ss-usa-odo01 ~]# /bin/cp -rf /usr/share/easy-rsa/2.0/* /etc/openvpn/easy-rsa
[root@ss-usa-odo01 ~]# cd /etc/openvpn/easy-rsa
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]# vi vars #参考下面的图做修改

[root@ss-usa-odo01 /etc/openvpn/easy-rsa]# source ./vars
NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys

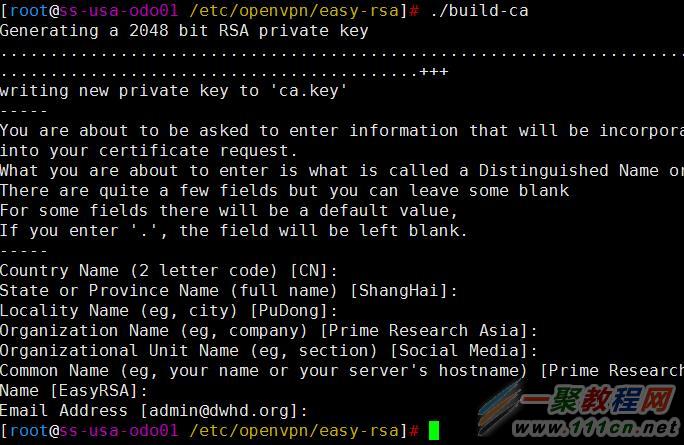
使用build-ca脚本构建CA证书,证书将创建在/etc/openvpn/easy-rsa/。按Enter键接受默认值:
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]# ./build-ca
Generating a 2048 bit RSA private key
.....................................................................+++
..........................................+++
writing new private key to 'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [ShangHai]:
Locality Name (eg, city) [PuDong]:
Organization Name (eg, company) [Prime Research Asia]:
Organizational Unit Name (eg, section) [Social Media]:
Common Name (eg, your name or your server's hostname) [Prime Research Asia CA]:
Name [EasyRSA]:
Email Address [admin@dwhd.org]:
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]#
下一步,我们将创建密钥和服务器本身的证书。和以前一样,接受默认值,然后按Y确认证书的签字:
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]# ./build-key-server server
Generating a 2048 bit RSA private key
............................+++
...................+++
writing new private key to 'server.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [ShangHai]:
Locality Name (eg, city) [PuDong]:
Organization Name (eg, company) [Prime Research Asia]:
Organizational Unit Name (eg, section) [Social Media]:
Common Name (eg, your name or your server's hostname) [server]:
Name [EasyRSA]:
Email Address [admin@dwhd.org]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /etc/openvpn/easy-rsa/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'ShangHai'
localityName :PRINTABLE:'PuDong'
organizationName :PRINTABLE:'Prime Research Asia'
organizationalUnitName:PRINTABLE:'Social Media'
commonName :PRINTABLE:'server'
name :PRINTABLE:'EasyRSA'
emailAddress :IA5STRING:'admin@dwhd.org'
Certificate is to be certified until Jun 11 18:27:02 2026 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]#
Linux之CentOS 7 安装openvpn
接下来,生成用于信息交流,以补充对RSA的Diffie-Hellman文件(这将需要相当长的一段时间)。这将创建一个名为dh2048.pem内的/ etc / OpenVPN的/ RSA /密钥文件中:
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]# ./build-dh
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
..................+.................
最后,为每个使用VPN服务器的客户端创建单独的证书文件:
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]# ./build-key 104.233.122.202-lookback
Generating a 2048 bit RSA private key
...+++
...........................................................+++
writing new private key to '104.233.122.202-lookback.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [ShangHai]:
Locality Name (eg, city) [PuDong]:
Organization Name (eg, company) [Prime Research Asia]:
Organizational Unit Name (eg, section) [Social Media]:
Common Name (eg, your name or your server's hostname) [104.233.122.202-lookback]:
Name [EasyRSA]:
Email Address [admin@dwhd.org]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /etc/openvpn/easy-rsa/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'ShangHai'
localityName :PRINTABLE:'PuDong'
organizationName :PRINTABLE:'Prime Research Asia'
organizationalUnitName:PRINTABLE:'Social Media'
commonName :PRINTABLE:'104.233.122.202-lookback'
name :PRINTABLE:'EasyRSA'
emailAddress :IA5STRING:'admin@dwhd.org'
Certificate is to be certified until Jun 11 18:35:47 2026 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]#
Linux之CentOS 7 安装openvpn
防止VPN被DDOS攻击,生成ta.key
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]# openvpn --genkey --secret ../ta.key
接下来开始修改server端的配置文件
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]# cp keys/{ca.crt,dh2048.pem,server.crt,server.key} /etc/openvpn/
[root@ss-usa-odo01 /etc/openvpn/easy-rsa]# cd ..
[root@ss-usa-odo01 /etc/openvpn]# vi server.conf
###下面是我的配置文件可以参考
[root@ss-usa-odo01 /etc/openvpn]# grep -Ev '^($|#)' server.conf
;local a.b.c.d #指定监听的本机IP(因为有些计算机具备多个IP地址),该命令是可选的,默认监听所有IP地址。
port 22033 #服务端端口号,根据需要自行修改
proto tcp #通过tcp协议来连接,也可以通过udp,看实际的需求
;proto udp
;dev tap
dev tun #路由模式,注意windows下必须使用dev tap
;dev-node MyTap #非Windows系统通常不需要设置这个
ca ca.crt #ca证书存放位置,这边是放在默认路径下的不需要修改,如果放在其他路径下,后面要加上绝对路径,根据实际情况更改
cert server.crt #服务器证书存放位置,这边是放在默认路径下的不需要修改,如果放在其他路径下,后面要加上绝对路径,根据实际情况更改
key server.key #服务器密钥存放位置,这边是放在默认路径下的不需要修改,如果放在其他路径下,后面要加上绝对路径,根据实际情况更改
dh dh2048.pem #dh2048.pem存放位置,这边是放在默认路径下的不需要修改,如果放在其他路径下,后面要加上绝对路径,根据实际情况更改
;topology subnet
server 10.188.0.0 255.255.0.0 #虚拟局域网网段设置,请根据需要自行修改
ifconfig-pool-persist ipp.txt #在openvpn重启时,再次连接的客户端将依然被分配和以前一样的IP地址
;server-bridge 10.8.0.4 255.255.255.0 10.8.0.50 10.8.0.100
;server-bridge
;push "route 192.168.10.0 255.255.255.0"
;push "route 192.168.20.0 255.255.255.0"
push "route 0.0.0.0 0.0.0.0" #全网走openvpn
;client-config-dir ccd
;route 192.168.40.128 255.255.255.248
;client-config-dir ccd
;route 10.9.0.0 255.255.255.252
;learn-address ./script
push "redirect-gateway def1 bypass-dhcp" #客户端所有网络通信通过vpn,这个可以选择的,如果注释掉的话那就是本地的数据包还是从本地出去,不强制走VPN
push "dhcp-option DNS 8.8.8.8" #指定客户端使用的主DNS
push "dhcp-option DNS 8.8.4.4" #指定客户端使用的备DNS
client-to-client #开启客户端互访
duplicate-cn #支持一个证书多个客户端登录使用,建议不启用
keepalive 5 30 #服务端5面监测一次,如果30秒没响应就认定客户端down了
tls-auth ta.key 0 #防DDOS攻击,服务器端0,客户端1
;cipher BF-CBC # Blowfish (default) #这是默认的加密算法
;cipher AES-128-CBC # AES
;cipher DES-EDE3-CBC # Triple-DES
comp-lzo #允许数据压缩,如果启用了客户端配置文件也需要有这项
max-clients 100 #最大客户端并发连接数量
user nobody #定义运行openvpn的用户
group nobody #定义运行openvpn的用户组
persist-key #通过keepalive检测超时后,重新启动VPN,不重新读取keys,保留第一次使用的keys
persist-tun #通过keepalive检测超时后,重新启动VPN,一直保持tun或者tap设备是linkup的,否则网络连接会先linkdown然后linkup
status /tmp/openvpn-status.log #定期把openvpn的一些状态信息写到文件中,以便自己写程序计费或者进行其他操作
;log openvpn.log #记录日志,每次重新启动openvpn后删除原有的log信息
log-append /tmp/openvpn.log #记录日志,每次重新启动openvpn后追加原有的log信息
verb 3 #设置日志要记录的级别,可选0-9,0 只记录错误信息,4 能记录普通的信息,5 和 6 在连接出现问题时能帮助调试,9 是极端的,所有信息都会显示,甚至连包头等信息都显示(像tcpdump)
mute 20
#相同信息的数量,如果连续出现 20 条相同的信息,将不记录到日志中。
[root@ss-usa-odo01 /etc/openvpn]#
[root@ss-usa-odo01 /etc/openvpn]# echo -e "###OpenVPN ADD\nnet.ipv4.conf.default.accept_source_route = 1\nnet.ipv4.conf.default.rp_filter = 0\nnet.ipv4.ip_forward = 1" >> /etc/sysctl.conf
[root@ss-usa-odo01 /etc/openvpn]# sysctl -p
net.ipv4.conf.default.accept_source_route = 1
net.ipv4.conf.default.rp_filter = 0
net.ipv4.ip_forward = 1
[root@ss-usa-odo01 /etc/openvpn]#
[root@ss-usa-odo01 /etc/openvpn]# systemctl -f enable openvpn@server
Created symlink from /etc/systemd/system/multi-user.target.wants/openvpn@server.service to /usr/lib/systemd/system/openvpn@.service.
[root@ss-usa-odo01 /etc/openvpn]# systemctl start openvpn@server
[root@ss-usa-odo01 /etc/openvpn]# systemctl -l status openvpn@server
● openvpn@server.service - OpenVPN Robust And Highly Flexible Tunneling Application On server
Loaded: loaded (/usr/lib/systemd/system/openvpn@.service; enabled; vendor preset: disabled)
Active: active (running) since 一 2016-06-13 16:08:20 EDT; 10s ago
Process: 6464 ExecStart=/usr/sbin/openvpn --daemon --writepid /var/run/openvpn/%i.pid --cd /etc/openvpn/ --config %i.conf (code=exited, status=0/SUCCESS)
Main PID: 6465 (openvpn)
CGroup: /system.slice/system-openvpn.slice/openvpn@server.service
└─6465 /usr/sbin/openvpn --daemon --writepid /var/run/openvpn/server.pid --cd /etc/openvpn/ --config server.conf
6月 13 16:08:20 ss-usa-odo01.90r.org systemd[1]: Starting OpenVPN Robust And Highly Flexible Tunneling Application On server...
6月 13 16:08:20 ss-usa-odo01.90r.org systemd[1]: Started OpenVPN Robust And Highly Flexible Tunneling Application On server.
[root@ss-usa-odo01 /etc/openvpn]# cat /tmp/openvpn.log
Mon Jun 13 16:07:47 2016 us=2075 Current Parameter Settings:
Mon Jun 13 16:07:47 2016 us=2135 config = 'server.conf'
Mon Jun 13 16:07:47 2016 us=2144 mode = 1
Mon Jun 13 16:07:47 2016 us=2150 persist_config = DISABLED
Mon Jun 13 16:07:47 2016 us=2156 persist_mode = 1
Mon Jun 13 16:07:47 2016 us=2162 show_ciphers = DISABLED
Mon Jun 13 16:07:47 2016 us=2168 show_digests = DISABLED
Mon Jun 13 16:07:47 2016 us=2174 show_engines = DISABLED
Mon Jun 13 16:07:47 2016 us=2180 genkey = DISABLED
Mon Jun 13 16:07:47 2016 us=2185 key_pass_file = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2192 show_tls_ciphers = DISABLED
Mon Jun 13 16:07:47 2016 us=2199 Connection profiles [default]:
Mon Jun 13 16:07:47 2016 us=2206 proto = tcp-server
Mon Jun 13 16:07:47 2016 us=2214 local = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2219 local_port = 22033
Mon Jun 13 16:07:47 2016 us=2224 remote = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2229 remote_port = 22033
Mon Jun 13 16:07:47 2016 us=2234 remote_float = DISABLED
Mon Jun 13 16:07:47 2016 us=2240 bind_defined = DISABLED
Mon Jun 13 16:07:47 2016 us=2246 bind_local = ENABLED
Mon Jun 13 16:07:47 2016 us=2252 connect_retry_seconds = 5
Mon Jun 13 16:07:47 2016 us=2258 connect_timeout = 10
Mon Jun 13 16:07:47 2016 us=2264 connect_retry_max = 0
Mon Jun 13 16:07:47 2016 us=2271 socks_proxy_server = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2277 socks_proxy_port = 0
Mon Jun 13 16:07:47 2016 us=2283 socks_proxy_retry = DISABLED
Mon Jun 13 16:07:47 2016 us=2289 tun_mtu = 1500
Mon Jun 13 16:07:47 2016 us=2305 tun_mtu_defined = ENABLED
Mon Jun 13 16:07:47 2016 us=2311 link_mtu = 1500
Mon Jun 13 16:07:47 2016 us=2316 link_mtu_defined = DISABLED
Mon Jun 13 16:07:47 2016 us=2322 tun_mtu_extra = 0
Mon Jun 13 16:07:47 2016 us=2327 tun_mtu_extra_defined = DISABLED
Mon Jun 13 16:07:47 2016 us=2333 mtu_discover_type = -1
Mon Jun 13 16:07:47 2016 us=2338 fragment = 0
Mon Jun 13 16:07:47 2016 us=2344 mssfix = 1450
Mon Jun 13 16:07:47 2016 us=2350 explicit_exit_notification = 0
Mon Jun 13 16:07:47 2016 us=2357 Connection profiles END
Mon Jun 13 16:07:47 2016 us=2363 remote_random = DISABLED
Mon Jun 13 16:07:47 2016 us=2368 ipchange = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2373 dev = 'tun'
Mon Jun 13 16:07:47 2016 us=2378 dev_type = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2382 dev_node = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2388 lladdr = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2394 topology = 1
Mon Jun 13 16:07:47 2016 us=2400 tun_ipv6 = DISABLED
Mon Jun 13 16:07:47 2016 us=2405 ifconfig_local = '10.188.0.1'
Mon Jun 13 16:07:47 2016 us=2411 ifconfig_remote_netmask = '10.188.0.2'
Mon Jun 13 16:07:47 2016 us=2416 ifconfig_noexec = DISABLED
Mon Jun 13 16:07:47 2016 us=2422 ifconfig_nowarn = DISABLED
Mon Jun 13 16:07:47 2016 us=2437 ifconfig_ipv6_local = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2442 ifconfig_ipv6_netbits = 0
Mon Jun 13 16:07:47 2016 us=2487 ifconfig_ipv6_remote = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2494 shaper = 0
Mon Jun 13 16:07:47 2016 us=2500 mtu_test = 0
Mon Jun 13 16:07:47 2016 us=2506 mlock = DISABLED
Mon Jun 13 16:07:47 2016 us=2512 keepalive_ping = 5
Mon Jun 13 16:07:47 2016 us=2518 keepalive_timeout = 30
Mon Jun 13 16:07:47 2016 us=2523 inactivity_timeout = 0
Mon Jun 13 16:07:47 2016 us=2537 ping_send_timeout = 5
Mon Jun 13 16:07:47 2016 us=2542 ping_rec_timeout = 60
Mon Jun 13 16:07:47 2016 us=2547 ping_rec_timeout_action = 2
Mon Jun 13 16:07:47 2016 us=2554 ping_timer_remote = DISABLED
Mon Jun 13 16:07:47 2016 us=2559 remap_sigusr1 = 0
Mon Jun 13 16:07:47 2016 us=2564 persist_tun = ENABLED
Mon Jun 13 16:07:47 2016 us=2569 persist_local_ip = DISABLED
Mon Jun 13 16:07:47 2016 us=2574 persist_remote_ip = DISABLED
Mon Jun 13 16:07:47 2016 us=2579 persist_key = ENABLED
Mon Jun 13 16:07:47 2016 us=2585 passtos = DISABLED
Mon Jun 13 16:07:47 2016 us=2590 resolve_retry_seconds = 1000000000
Mon Jun 13 16:07:47 2016 us=2596 username = 'nobody'
Mon Jun 13 16:07:47 2016 us=2601 groupname = 'nobody'
Mon Jun 13 16:07:47 2016 us=2617 chroot_dir = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2622 cd_dir = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2627 writepid = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2645 up_script = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2650 down_script = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2655 down_pre = DISABLED
Mon Jun 13 16:07:47 2016 us=2660 up_restart = DISABLED
Mon Jun 13 16:07:47 2016 us=2668 up_delay = DISABLED
Mon Jun 13 16:07:47 2016 us=2675 daemon = DISABLED
Mon Jun 13 16:07:47 2016 us=2681 inetd = 0
Mon Jun 13 16:07:47 2016 us=2686 log = ENABLED
Mon Jun 13 16:07:47 2016 us=2692 suppress_timestamps = DISABLED
Mon Jun 13 16:07:47 2016 us=2696 nice = 0
Mon Jun 13 16:07:47 2016 us=2701 verbosity = 6
Mon Jun 13 16:07:47 2016 us=2706 mute = 0
Mon Jun 13 16:07:47 2016 us=2711 gremlin = 0
Mon Jun 13 16:07:47 2016 us=2716 status_file = '/tmp/openvpn-status.log'
Mon Jun 13 16:07:47 2016 us=2721 status_file_version = 1
Mon Jun 13 16:07:47 2016 us=2727 status_file_update_freq = 60
Mon Jun 13 16:07:47 2016 us=2732 occ = ENABLED
Mon Jun 13 16:07:47 2016 us=2738 rcvbuf = 0
Mon Jun 13 16:07:47 2016 us=2743 sndbuf = 0
Mon Jun 13 16:07:47 2016 us=2749 mark = 0
Mon Jun 13 16:07:47 2016 us=2754 sockflags = 0
Mon Jun 13 16:07:47 2016 us=2759 fast_io = DISABLED
Mon Jun 13 16:07:47 2016 us=2765 lzo = 7
Mon Jun 13 16:07:47 2016 us=2773 route_script = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2779 route_default_gateway = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2784 route_default_metric = 0
Mon Jun 13 16:07:47 2016 us=2791 route_noexec = DISABLED
Mon Jun 13 16:07:47 2016 us=2797 route_delay = 0
Mon Jun 13 16:07:47 2016 us=2803 route_delay_window = 30
Mon Jun 13 16:07:47 2016 us=2809 route_delay_defined = DISABLED
Mon Jun 13 16:07:47 2016 us=2815 route_nopull = DISABLED
Mon Jun 13 16:07:47 2016 us=2820 route_gateway_via_dhcp = DISABLED
Mon Jun 13 16:07:47 2016 us=2826 max_routes = 100
Mon Jun 13 16:07:47 2016 us=2831 allow_pull_fqdn = DISABLED
Mon Jun 13 16:07:47 2016 us=2838 route 10.188.0.0/255.255.0.0/nil/nil
Mon Jun 13 16:07:47 2016 us=2843 management_addr = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2850 management_port = 0
Mon Jun 13 16:07:47 2016 us=2856 management_user_pass = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2862 management_log_history_cache = 250
Mon Jun 13 16:07:47 2016 us=2877 management_echo_buffer_size = 100
Mon Jun 13 16:07:47 2016 us=2883 management_write_peer_info_file = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2889 management_client_user = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2895 management_client_group = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2901 management_flags = 0
Mon Jun 13 16:07:47 2016 us=2912 shared_secret_file = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=2918 key_direction = 1
Mon Jun 13 16:07:47 2016 us=2924 ciphername_defined = ENABLED
Mon Jun 13 16:07:47 2016 us=2940 ciphername = 'BF-CBC'
Mon Jun 13 16:07:47 2016 us=2946 authname_defined = ENABLED
Mon Jun 13 16:07:47 2016 us=2951 authname = 'SHA1'
Mon Jun 13 16:07:47 2016 us=2957 prng_hash = 'SHA1'
Mon Jun 13 16:07:47 2016 us=2963 prng_nonce_secret_len = 16
Mon Jun 13 16:07:47 2016 us=2968 keysize = 0
Mon Jun 13 16:07:47 2016 us=2974 engine = DISABLED
Mon Jun 13 16:07:47 2016 us=2979 replay = ENABLED
Mon Jun 13 16:07:47 2016 us=2989 mute_replay_warnings = DISABLED
Mon Jun 13 16:07:47 2016 us=2994 replay_window = 64
Mon Jun 13 16:07:47 2016 us=2999 replay_time = 15
Mon Jun 13 16:07:47 2016 us=3004 packet_id_file = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3010 use_iv = ENABLED
Mon Jun 13 16:07:47 2016 us=3015 test_crypto = DISABLED
Mon Jun 13 16:07:47 2016 us=3020 tls_server = ENABLED
Mon Jun 13 16:07:47 2016 us=3026 tls_client = DISABLED
Mon Jun 13 16:07:47 2016 us=3031 key_method = 2
Mon Jun 13 16:07:47 2016 us=3047 ca_file = 'ca.crt'
Mon Jun 13 16:07:47 2016 us=3053 ca_path = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3069 dh_file = 'dh2048.pem'
Mon Jun 13 16:07:47 2016 us=3074 cert_file = 'server.crt'
Mon Jun 13 16:07:47 2016 us=3080 extra_certs_file = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3096 priv_key_file = 'server.key'
Mon Jun 13 16:07:47 2016 us=3102 pkcs12_file = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3107 cipher_list = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3112 tls_verify = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3118 tls_export_cert = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3123 verify_x509_type = 0
Mon Jun 13 16:07:47 2016 us=3129 verify_x509_name = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3135 crl_file = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3140 ns_cert_type = 0
Mon Jun 13 16:07:47 2016 us=3146 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3152 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3157 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3163 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3169 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3174 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3179 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3184 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3189 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3194 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3199 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3204 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3209 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3214 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3220 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3234 remote_cert_ku[i] = 0
Mon Jun 13 16:07:47 2016 us=3241 remote_cert_eku = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3246 ssl_flags = 0
Mon Jun 13 16:07:47 2016 us=3252 tls_timeout = 2
Mon Jun 13 16:07:47 2016 us=3258 renegotiate_bytes = 0
Mon Jun 13 16:07:47 2016 us=3263 renegotiate_packets = 0
Mon Jun 13 16:07:47 2016 us=3268 renegotiate_seconds = 3600
Mon Jun 13 16:07:47 2016 us=3274 handshake_window = 60
Mon Jun 13 16:07:47 2016 us=3278 transition_window = 3600
Mon Jun 13 16:07:47 2016 us=3293 single_session = DISABLED
Mon Jun 13 16:07:47 2016 us=3298 push_peer_info = DISABLED
Mon Jun 13 16:07:47 2016 us=3303 tls_exit = DISABLED
Mon Jun 13 16:07:47 2016 us=3309 tls_auth_file = 'ta.key'
Mon Jun 13 16:07:47 2016 us=3315 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3321 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3327 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3332 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3338 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3344 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3350 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3356 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3361 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3367 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3372 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3377 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3382 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3389 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3395 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3403 pkcs11_protected_authentication = DISABLED
Mon Jun 13 16:07:47 2016 us=3410 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3415 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3421 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3426 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3432 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3437 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3443 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3448 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3454 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3459 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3465 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3481 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3486 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3503 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3509 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3514 pkcs11_private_mode = 00000000
Mon Jun 13 16:07:47 2016 us=3530 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3535 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3540 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3545 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3550 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3557 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3563 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3568 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3573 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3579 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3585 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3590 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3595 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3601 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3606 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3613 pkcs11_cert_private = DISABLED
Mon Jun 13 16:07:47 2016 us=3619 pkcs11_pin_cache_period = -1
Mon Jun 13 16:07:47 2016 us=3624 pkcs11_id = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3630 pkcs11_id_management = DISABLED
Mon Jun 13 16:07:47 2016 us=3637 server_network = 10.188.0.0
Mon Jun 13 16:07:47 2016 us=3643 server_netmask = 255.255.0.0
Mon Jun 13 16:07:47 2016 us=3654 server_network_ipv6 = ::
Mon Jun 13 16:07:47 2016 us=3660 server_netbits_ipv6 = 0
Mon Jun 13 16:07:47 2016 us=3666 server_bridge_ip = 0.0.0.0
Mon Jun 13 16:07:47 2016 us=3672 server_bridge_netmask = 0.0.0.0
Mon Jun 13 16:07:47 2016 us=3678 server_bridge_pool_start = 0.0.0.0
Mon Jun 13 16:07:47 2016 us=3685 server_bridge_pool_end = 0.0.0.0
Mon Jun 13 16:07:47 2016 us=3690 push_entry = 'route 0.0.0.0 0.0.0.0'
Mon Jun 13 16:07:47 2016 us=3708 push_entry = 'redirect-gateway def1 bypass-dhcp'
Mon Jun 13 16:07:47 2016 us=3724 push_entry = 'dhcp-option DNS 8.8.8.8'
Mon Jun 13 16:07:47 2016 us=3729 push_entry = 'dhcp-option DNS 8.8.4.4'
Mon Jun 13 16:07:47 2016 us=3734 push_entry = 'route 10.188.0.0 255.255.0.0'
Mon Jun 13 16:07:47 2016 us=3740 push_entry = 'topology net30'
Mon Jun 13 16:07:47 2016 us=3747 push_entry = 'ping 5'
Mon Jun 13 16:07:47 2016 us=3751 push_entry = 'ping-restart 30'
Mon Jun 13 16:07:47 2016 us=3754 ifconfig_pool_defined = ENABLED
Mon Jun 13 16:07:47 2016 us=3758 ifconfig_pool_start = 10.188.0.4
Mon Jun 13 16:07:47 2016 us=3762 ifconfig_pool_end = 10.188.255.251
Mon Jun 13 16:07:47 2016 us=3766 ifconfig_pool_netmask = 0.0.0.0
Mon Jun 13 16:07:47 2016 us=3769 ifconfig_pool_persist_filename = 'ipp.txt'
Mon Jun 13 16:07:47 2016 us=3773 ifconfig_pool_persist_refresh_freq = 600
Mon Jun 13 16:07:47 2016 us=3776 ifconfig_ipv6_pool_defined = DISABLED
Mon Jun 13 16:07:47 2016 us=3780 ifconfig_ipv6_pool_base = ::
Mon Jun 13 16:07:47 2016 us=3783 ifconfig_ipv6_pool_netbits = 0
Mon Jun 13 16:07:47 2016 us=3790 n_bcast_buf = 256
Mon Jun 13 16:07:47 2016 us=3793 tcp_queue_limit = 64
Mon Jun 13 16:07:47 2016 us=3796 real_hash_size = 256
Mon Jun 13 16:07:47 2016 us=3800 virtual_hash_size = 256
Mon Jun 13 16:07:47 2016 us=3803 client_connect_script = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3807 learn_address_script = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3810 client_disconnect_script = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3814 client_config_dir = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3817 ccd_exclusive = DISABLED
Mon Jun 13 16:07:47 2016 us=3820 tmp_dir = '/tmp'
Mon Jun 13 16:07:47 2016 us=3824 push_ifconfig_defined = DISABLED
Mon Jun 13 16:07:47 2016 us=3828 push_ifconfig_local = 0.0.0.0
Mon Jun 13 16:07:47 2016 us=3831 push_ifconfig_remote_netmask = 0.0.0.0
Mon Jun 13 16:07:47 2016 us=3835 push_ifconfig_ipv6_defined = DISABLED
Mon Jun 13 16:07:47 2016 us=3841 push_ifconfig_ipv6_local = ::/0
Mon Jun 13 16:07:47 2016 us=3845 push_ifconfig_ipv6_remote = ::
Mon Jun 13 16:07:47 2016 us=3849 enable_c2c = ENABLED
Mon Jun 13 16:07:47 2016 us=3853 duplicate_cn = ENABLED
Mon Jun 13 16:07:47 2016 us=3858 cf_max = 0
Mon Jun 13 16:07:47 2016 us=3862 cf_per = 0
Mon Jun 13 16:07:47 2016 us=3865 max_clients = 100
Mon Jun 13 16:07:47 2016 us=3869 max_routes_per_client = 256
Mon Jun 13 16:07:47 2016 us=3882 auth_user_pass_verify_script = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3886 auth_user_pass_verify_script_via_file = DISABLED
Mon Jun 13 16:07:47 2016 us=3889 port_share_host = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3893 port_share_port = 0
Mon Jun 13 16:07:47 2016 us=3896 client = DISABLED
Mon Jun 13 16:07:47 2016 us=3900 pull = DISABLED
Mon Jun 13 16:07:47 2016 us=3906 auth_user_pass_file = '[UNDEF]'
Mon Jun 13 16:07:47 2016 us=3911 OpenVPN 2.3.11 x86_64-redhat-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [MH] [IPv6] built on May 10 2016
Mon Jun 13 16:07:47 2016 us=3919 library versions: OpenSSL 1.0.1e-fips 11 Feb 2013, LZO 2.06
Mon Jun 13 16:07:47 2016 us=4002 WARNING: --ifconfig-pool-persist will not work with --duplicate-cn
Mon Jun 13 16:07:47 2016 us=59407 Diffie-Hellman initialized with 2048 bit key
Mon Jun 13 16:07:47 2016 us=59920 Control Channel Authentication: using 'ta.key' as a OpenVPN static key file
Mon Jun 13 16:07:47 2016 us=59938 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Jun 13 16:07:47 2016 us=59946 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Jun 13 16:07:47 2016 us=59958 TLS-Auth MTU parms [ L:1544 D:1182 EF:68 EB:0 ET:0 EL:3 ]
Mon Jun 13 16:07:47 2016 us=59975 Socket Buffers: R=[87380->87380] S=[16384->16384]
Mon Jun 13 16:07:47 2016 us=60070 ROUTE_GATEWAY ON_LINK IFACE=venet0 HWADDR=00:00:00:00:00:00
Mon Jun 13 16:07:47 2016 us=60296 TUN/TAP device tun0 opened
Mon Jun 13 16:07:47 2016 us=60311 TUN/TAP TX queue length set to 100
Mon Jun 13 16:07:47 2016 us=60323 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Mon Jun 13 16:07:47 2016 us=60341 /usr/sbin/ip link set dev tun0 up mtu 1500
Mon Jun 13 16:07:47 2016 us=72043 /usr/sbin/ip addr add dev tun0 local 10.188.0.1 peer 10.188.0.2
Mon Jun 13 16:07:47 2016 us=89355 /usr/sbin/ip route add 10.188.0.0/16 via 10.188.0.2
Mon Jun 13 16:07:47 2016 us=90077 Data Channel MTU parms [ L:1544 D:1450 EF:44 EB:143 ET:0 EL:3 AF:3/1 ]
Mon Jun 13 16:07:47 2016 us=90257 GID set to nobody
Mon Jun 13 16:07:47 2016 us=90268 UID set to nobody
Mon Jun 13 16:07:47 2016 us=90275 Listening for incoming TCP connection on [undef]
Mon Jun 13 16:07:47 2016 us=90283 TCPv4_SERVER link local (bound): [undef]
Mon Jun 13 16:07:47 2016 us=90287 TCPv4_SERVER link remote: [undef]
Mon Jun 13 16:07:47 2016 us=90295 MULTI: multi_init called, r=256 v=256
Mon Jun 13 16:07:47 2016 us=90441 IFCONFIG POOL: base=10.188.0.4 size=16382, ipv6=0
Mon Jun 13 16:07:47 2016 us=90453 IFCONFIG POOL LIST
Mon Jun 13 16:07:47 2016 us=90480 MULTI: TCP INIT maxclients=100 maxevents=104
Mon Jun 13 16:07:47 2016 us=90495 Initialization Sequence Completed
Mon Jun 13 16:08:07 2016 us=790588 TCP/UDP: Closing socket
Mon Jun 13 16:08:07 2016 us=790658 /usr/sbin/ip route del 10.188.0.0/16
RTNETLINK answers: Operation not permitted
Mon Jun 13 16:08:07 2016 us=791611 ERROR: Linux route delete command failed: external program exited with error status: 2
Mon Jun 13 16:08:07 2016 us=791637 Closing TUN/TAP interface
Mon Jun 13 16:08:07 2016 us=791657 /usr/sbin/ip addr del dev tun0 local 10.188.0.1 peer 10.188.0.2
RTNETLINK answers: Operation not permitted
Mon Jun 13 16:08:07 2016 us=792360 Linux ip addr del failed: external program exited with error status: 2
Mon Jun 13 16:08:07 2016 us=830989 SIGINT[hard,] received, process exiting
[root@ss-usa-odo01 /etc/openvpn]#
[root@ss-usa-odo01 /etc/openvpn]# iptables -nvxL --lin
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 127988 174103095 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
3 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
4 228 14272 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
5 651 33525 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 77183 packets, 5938860 bytes)
num pkts bytes target prot opt in out source destination
[root@ss-usa-odo01 /etc/openvpn]# iptables -I INPUT 4 -p tcp -m state --state NEW -m tcp --dport 22033 -j ACCEPT
[root@ss-usa-odo01 /etc/openvpn]# iptables -nvxL --lin
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 127988 174103095 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
3 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
4 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22033
5 228 14272 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
6 651 33525 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 77183 packets, 5938860 bytes)
num pkts bytes target prot opt in out source destination
[root@ss-usa-odo01 /etc/openvpn]# iptables -I FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
[root@ss-usa-odo01 /etc/openvpn]# iptables -I FORWARD 2 -s 10.0.0.0/8 -j ACCEPT
[root@ss-usa-odo01 /etc/openvpn]# iptables -nvxL --lin
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 128015 174104967 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
3 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
4 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22033
5 228 14272 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
6 651 33525 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2 0 0 ACCEPT all -- * * 10.0.0.0/8 0.0.0.0/0
3 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 3 packets, 436 bytes)
num pkts bytes target prot opt in out source destination
[root@ss-usa-odo01 /etc/openvpn]# iptables -t nat -A POSTROUTING -s 10.0.0.0/8 -j SNAT --to-source 104.223.122.202
[root@ss-usa-odo01 /etc/openvpn]# iptables -t nat -nvxL --lin
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 SNAT all -- * * 10.0.0.0/8 0.0.0.0/0 to:104.223.122.202
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
[root@ss-usa-odo01 /etc/openvpn]# iptables-save >/etc/sysconfig/iptables
[root@ss-usa-odo01 /etc/openvpn]# cat /etc/sysconfig/iptables
# Generated by iptables-save v1.4.21 on Mon Jun 13 16:14:40 2016
*raw
:PREROUTING ACCEPT [366072:522504090]
:OUTPUT ACCEPT [204986:14628967]
COMMIT
# Completed on Mon Jun 13 16:14:40 2016
# Generated by iptables-save v1.4.21 on Mon Jun 13 16:14:40 2016
*nat
:PREROUTING ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A POSTROUTING -s 10.0.0.0/8 -j SNAT --to-source 104.223.122.202
COMMIT
# Completed on Mon Jun 13 16:14:40 2016
# Generated by iptables-save v1.4.21 on Mon Jun 13 16:14:40 2016
*mangle
:PREROUTING ACCEPT [366072:522504090]
:INPUT ACCEPT [366072:522504090]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [204986:14628967]
:POSTROUTING ACCEPT [204986:14628967]
COMMIT
# Completed on Mon Jun 13 16:14:40 2016
# Generated by iptables-save v1.4.21 on Mon Jun 13 16:14:40 2016
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [98:11832]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22033 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -s 10.0.0.0/8 -j ACCEPT
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
# Completed on Mon Jun 13 16:14:40 2016
[root@ss-usa-odo01 /etc/openvpn]#
iptables -nvxL --lin
iptables -I INPUT 4 -p tcp -m state --state NEW -m tcp --dport 22033 -j ACCEPT
iptables -I FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -I FORWARD 2 -s 10.0.0.0/8 -j ACCEPT
iptables -t nat -A POSTROUTING -s 10.0.0.0/8 -j SNAT --to-source 104.223.122.202
iptables-save >/etc/sysconfig/iptables
###由于OpenVPN本事不支持多端口,因此我们可以借助iptables来实现多端口使用
iptables -t nat -A PREROUTING -p tcp -d 104.223.122.202 -m multiport --dports 22034:22044 -j REDIRECT --to-port 22033
这样就把所有发往104.223.122.202这个Ip的22034-22044端口的数据包都转发到了22033上了
104.223.122.202是你的OpenVPN的监听IP
客户端配置文件参考
client
dev tun
proto tcp
resolv-retry infinite
nobind
persist-key
persist-tun
comp-lzo
verb 3
remote 104.223.122.202 22033
ca 104.223.122.202-ca.crt
cert 104.223.122.202-lookback.crt
key 104.223.122.202-lookback.key
tls-auth 104.223.122.202-ta.key 1





